In order to make this work, check out the Prerequisites section, and read my other articles about installing and configuring AD FS prior to setting them up with ShareFile and/or NetScaler. This setup requires multiple steps with functional verification tests in between each step in order to minimize sources of error.
Prerequisites:
- Public Signed Server Certificate adfs.domain.com
- Firewall configuration allowing external traffic destined for your internal AD FS server to pass through (https, Port 443)
- AD FS 2.0 downloadable installer (for Microsoft Windows Server 2008 and 2008 R2)
- Internet Information Services (IIS) 7 or 7.5 Server Role installed (for Microsoft Windows Server 2008 and 2008 R2)
- AD FS 3.0 Server Role installed (for Microsoft Windows Server 2012 R2)
- Internet Information Services (IIS) 8.5 Server Role installed (for Microsoft Windows Server 2012 R2)
- .NET Framework 3.5 SP1 Feature installed
- SQL Server 2005 (Express, Standard, Enterprise), SQL Server 2008 (Express, Standard, Enterprise), or Windows Internal Database
Detailed HowTo’s for AD FS Installation and Configuration can be found here:
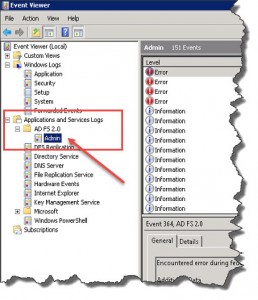
AD FS related errors can be found in the Event Log by expanding the Applications and Services Logs node, and navigating to AD FS 2.0 \ Admin (for Windows Server 2008 and 2008 R2):
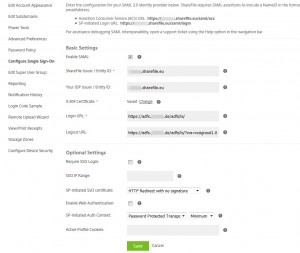
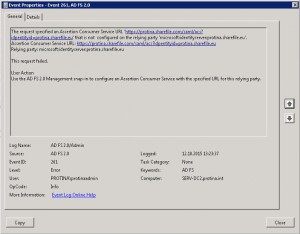
My working ShareFile Single sign-on / SAML 2.0 Configuration with AD FS 2.0 looks like this:
Testing your setup:
- https://mydomain.sharefile.com/saml/login
- https://adfs.mydomain.com/adfs/ls
- https://adfs.mydomain.com/adfs/ls/IdpInitiatedSignOn.aspx
Lessons learned during my configuration
Error Signin ADFS:
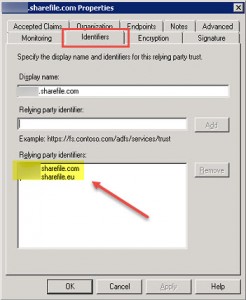
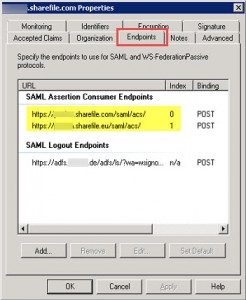
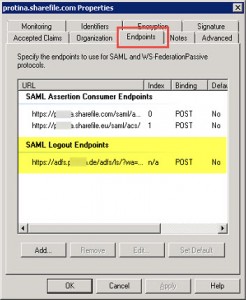
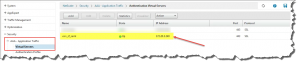
Add corresponding ShareFile Subdomain URLs to Relying Party Trusts configuration (in my case I had to add both sharefile.com and sharefile.eu TLDs):
- Tab: Identifiers
- Tab: Endpoints
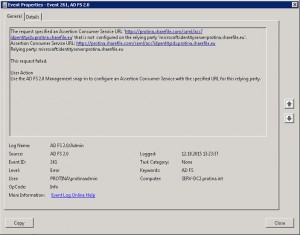
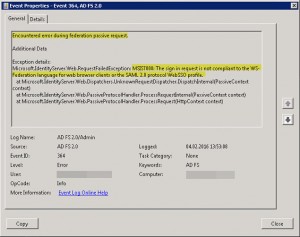
Error Signin ADFS:
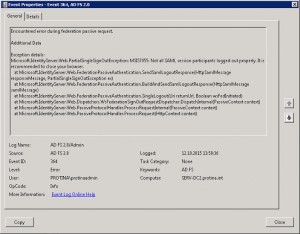
Event Log Error, Event ID 364, Source: AD FS 2.0, Error Number: MSIS7000
Have a look at TechNet – Troubleshooting Fedpassive request failures with AD FS 2.0
Encountered error during federation passive request.
Additional Data
Exception details:
Microsoft.IdentityServer.Web.RequestFailedException: MSIS7000: The sign in request is not compliant to the WS-Federation language for web browser clients or the SAML 2.0 protocol WebSSO profile.
at Microsoft.IdentityServer.Web.Dispatchers.UnknownRequestDispatcher.DispatchInternal(PassiveContext context)
at Microsoft.IdentityServer.Web.PassiveProtocolHandler.ProcessRequestInternal(PassiveContext context)
at Microsoft.IdentityServer.Web.PassiveProtocolHandler.ProcessRequest(HttpContext context)
I found something interesting at Windows Identity Foundation 101’s : WS-Federation Passive Requestor Profile (part 1 of 2), when searching for MSIS7000:
ADFS v2 does not support WS-Federation POST sign-in, only GET.
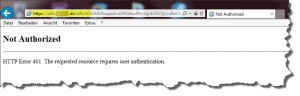
HTTP Error 401. The requested resource requires user authentication
It turned out I had to start the AD FS service with proper credentials. As I had issues with launching the service, I switched it to LOCAL SYSTEM, which in return caused this particular issue. So, first I had to remedy the issue of failed service start by configuring the SPN for the service account, and providing internet access to my AD FS server in order to enable querying if CRL through .NET. Then I adjusted the corresponding Application Pool in IIS on my AD FS server in order to reflect the AD FS service’s account. In the end I was able to start the service properly. Afterwards SAML SSO from internal networks worked as well.
Have a look at:
- TechNet – AD FS 2.0: How to Change the Local Authentication Type
- TechNet – AD FS 2.0: How to Configure the SPN (servicePrincipalName) for the Service Account
- TechNet – AD FS 2.0: The Service Fails to Start: “The service did not respond to the start or control request in a timely fashion.”
- TechNet – AD FS 2.0: Windows service does not start, does not start automatically, or starts slowly
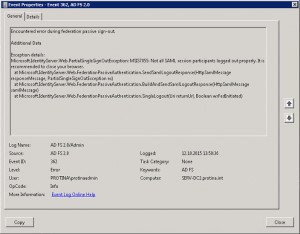
Error Signout ADFS:
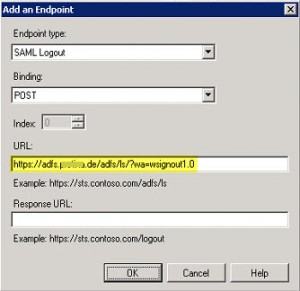
Add Logout URL to Relying Party Trusts configuration:
- Tab: Endpoints
- Endpoint Tpye: SAML Logout
- Binding: POST
- URL: https://adfs.domain.de/adfs/ls/?wa=wsignout1.0
Now as we have successfully configured a working SSO environment using ShareFile and AD FS, we can go the extra mile and add NetScaler to the equation, of course as a means of security enhancement. As you should never ever expose an ADFS server to the internet, you could use NetScaler as a Proxy. Read more about in my blog article https://blog.ollischer.com/citrix-netscaler-v11-how-to-setup-your-netscaler-as-an-ad-fs-proxy.
Errors:
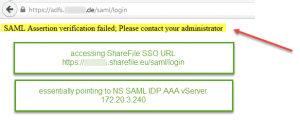
- “SAML Assertion verification failed; Please contact your administrator“, i.e. incorrect IDP certificate configured on NetScaler
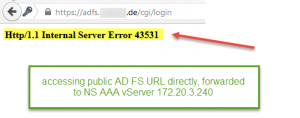
- Http/1.1 Internal Server Error 43531
Run one of the following commands from the shell prompt of the NS to view the real time hits on the (as per CTX138840)
- authentication policies and session policies applied on the NS Gateway vServer:
nsconmsg –d current –g pol_hits
- rewrite policy bound at a global level or to a load balancing, content switching, or NS Gateway vServer:
nsconmsg –d current | egrep –i rewrite
- responder policy bound at a global level or to a load balancing, content switching, or NS Gateway vServer:
nsconmsg –d current | egrep –i responder
In order to troubleshoot authentication with Aaad.debug (as per CTX114999) run the following command from the shell prompt of the NS:
- cd /tmp
- cat aaad.debug
Another Event ID 364 error message:
- MSIS2001: Configuration service URL is not configured.
- MSIS7012: An error occurred while processing the request. Contact your administrator for details
After checkings the AD FS 2.0 service I discovered that it was not running. When trying to start the service it did not start and subsequent Events 7000 and 70009 were logged in Event Log Viewer. It turned out that the server hosting AD FS 2.0 need internet access or you need to disable generatePublisherEvidence for .NET 3.5. See:
- The Service Fails to Start: “The service did not respond to the start or control request in a timely fashion.”
- Unable to start the AD FS 2.0 Windows service due to service timeout
Service Control Manager (SCM) is timing out the service start before it is complete. This is usually due to lack of internet connectivity from the AD FS 2.0 Federation Server or AD FS 2.0 Federation Server Proxy. At service start, when generatePublisherEvidence is enabled for .NET 3.5, the server will attempt to connect to crl.microsoft.com over TCP port 80. AD FS 2.0 does not rely on a positive or negative response from generatePublisherEvidence, and the default value can cause Service Control Manager to time out while waiting on the TCP/80 connection to fail to connect to crl.microsoft.com.
Further reading:
- Citrix Blogs – SAML authentication with ShareFile using AD FS 2.0
- Andrew Morgan – Configuring ShareFile and SAML Walkthrough
- Jason Samuel – How to setup Citrix ShareFile single sign-on using SAML IDP on NetScaler
- Configure ShareFile Single Sign-On with ADFS
- ShareFile Custom Login Screen
- Technet Forums – ADFS and Google Apps SSO – Signout URL?
- CTX133919 – How to Configure NetScaler SAML to Work with Microsoft AD FS 2.0 IDP
- CTX200323 – SAML Integration between NetScaler and ShareFile
- CTX208557 – ShareFile Single Sign-On SSO
- Citrix Blogs – ADFS v3 on Windows Server 2012 R2 with NetScaler
- ShareFile SAML Authentifizierungs mit Microsoft ADFS – Teil 2: ADFS 2.0 [German]
- Jay Simcox – Beginners Guide to Claims-based Authentication, AD FS 3.0, and SharePoint 2013 – Part II: Installing and Configuring AD FS 3.0
- Cividan IT Blog – Use Citrix Netscaler as a replacement for ADFS Proxy
- Citrix – NetScaler as ADFS Proxy Deployment Guide

Pingback: HowTo – Install and Configure Microsoft Active Directory Federation Services 3.0 (ADFS 3.0) – blog – Alexander Ollischer | Citrix | Microsoft