I had quite some trouble installing and configuring AD FS 3.0 on a Windows Server 2012 R2 with a SQL Server 2005 Standard Edition server to store my Configuration DB in. Therefore I wanted to share that information, hoping it might be useful to others as well.
- Prerequisites
- Install IIS Role
- Configure IIS Default Web Site Binding (Port 443)
- Install AD FS Role
- Configure AD FS Role
- Verify AD FS Role functionality
- Troubleshooting AD FS Role
Prerequisites as per Microsoft:
- Certificate Requirements for Federation Servers
- Name Resolution Requirements for Federation Servers
- Join a Computer to a Domain
- Add a Host (A) Resource Record to Corporate DNS for a Federation Server
- Import a Server Authentication Certificate to the Default Web Site
- Configure a Service Account for a Federation Server Farm
Install Windows Server 2012 R2 IIS Role:
Install IIS 8.5 components required by AD FS with Powershell:
Import-Module ServerManager
Install-WindowsFeature -Name Web-Server, Web-WebServer, Web-Mgmt-Tools
Import appropiate Server Authentication Certificate (aka SSL Certificate) into IIS
The following requirements must be met in order to use the SSL Certificate for AD FS:
- Subject name and subject alternative name (SAN) must contain your federation service name, such as adfs.domain.com.
- Subject alternative name (SAN) must contain the value enterpriseregistration followed by the UPN suffix of your organization, such as, for example, enterpriseregistration.domain.com.
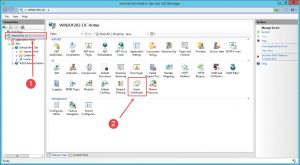
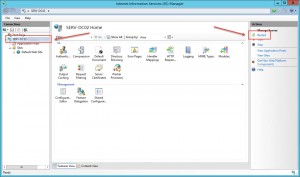
- Open Internet Information Services (IIS) Manager console.
- Highlight your Server node.
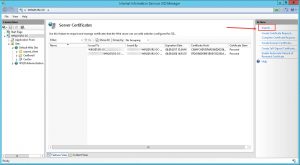
- Click Server Certificates in the middle pane.

- Then click Import in the right Actions pane.

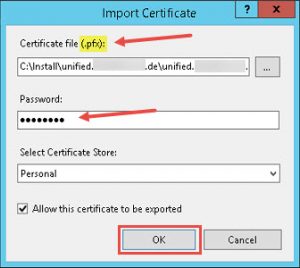
- Browse to your corresponding Server Certificate (must be in pfx file format and thus include a private key), provide the Private Key’s password and click OK.

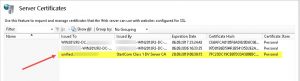
- The newly imported Server Certificate should now be available for the subsequent https binding.

Configure https binding for Default Web Site in IIS:
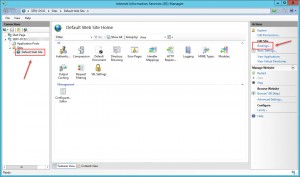
- Open Internet Information Services (IIS) Manager console.
- Expand your Server node, drill down to your Default Web Site node and highlight it.
- Hit Bindings in the right Actions pane:

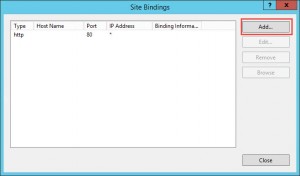
- Hit Add… in the Site Bindings dialogue:

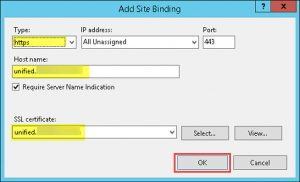
- Select https in the Type drop down field and your corresponding server certificate in the SSL certificate drop down field. Provide a Host Name, e.g. sso.domain.com or adfs.domain.com (which must be identical to the Server Certificate’s name or part of its SANs). Click OK:

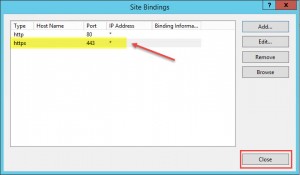
- Close the Site Bindings dialogue window:

- Restart IIS:

Keep in mind that IIS 8.5 supports Server Name Indication (SNI), i.e. it allows you to install multiple SSL certificates on Microsoft IIS 8.5. In case you missed a certain SAN on the Server Certificate you are now able to add/change FQDNs even afterwards. Check out Federation with ADFS 3.0 and SNI Support for further details.
Install Windows Server 2012 R2 AD FS Role:
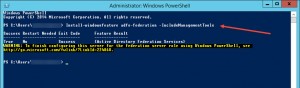
Install AD FS Role with Powershell:
Install-WindowsFeature adfs-federation -IncludeManagementTools
Basic configuration of AD FS:
Decide whether you’re going to use Windows Internal Database or a dedicated Microsoft SQL Server to store the AD FS Configuration DB. I chose an existing Microsoft SQL Server 2005 Standard Edition (German Language Setup). And that’s where the trouble began…
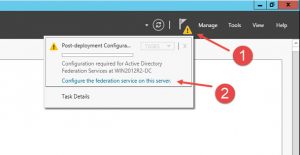
- Initiate the Active Directory Federation Services Configuration Wizard from within Server Manager:

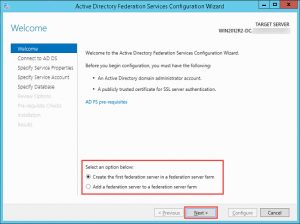
- Choose whether you want to deploy a new Federation Server Farm or add additional servers to an existing Federation Server Farm and click Next:

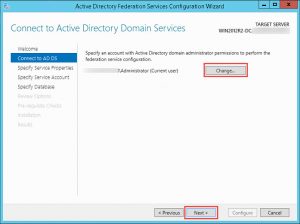
- Select an account with appropiate permissions in order to configure the AD FS service and click Next:

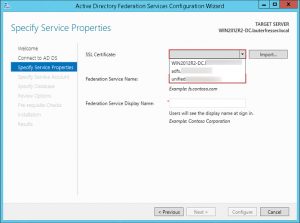
- Choose the corresponding SSL Certificate from the drop down list next to SSL Certificate:

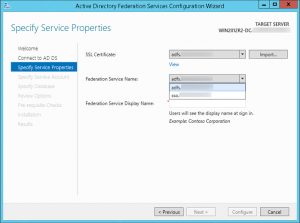
- Choose a matching Subject Alternate Name (SAN) from the drop down list next to Federation Service Name:

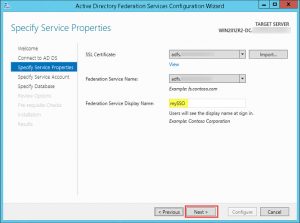
- Enter your Federation Service Display Name and click Next:

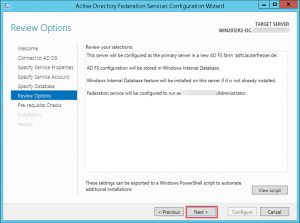
- Review your settings and start configuration by clicking Next:

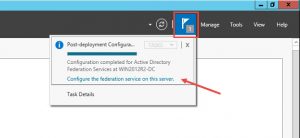
- After a successful configuration launch the AD FS Management Console:

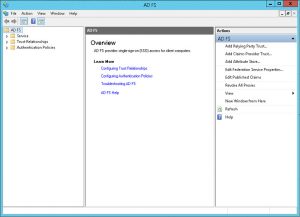
- During first launch it should look something like this:

- Basic setup is now complete.
Final configuration tasks with Powershell when using a SQL Server database:
Import-Module ADFS
# Get the credential used for the federation service account
$serviceAccountCredential = Get-Credential -Message “Enter the credential for the Federation Service Account.”Install-AdfsFarm `
-CertificateThumbprint:”769F17D6142B17F831943A9428903C79FD1EF9B9″ `
-FederationServiceDisplayName:”adfs.domain.com” `
-FederationServiceName:”mySSO” `
-ServiceAccountCredential:$serviceAccountCredential `
-SQLConnectionString:”Data Source=SERV-DB;Initial Catalog=ADFSConfiguration;Integrated Security=True;Min Pool Size=20″
Final configuration tasks with Powershell when using a Windows Internal Database:
Import-Module ADFS
# Get the credential used for the federation service account
$serviceAccountCredential = Get-Credential -Message “Enter the credential for the Federation Service Account.”Install-AdfsFarm `
-CertificateThumbprint:”7FC23DC19CB07D33A30965C794FAD96ABD3396D9″ `
-FederationServiceDisplayName:”mySSO” `
-FederationServiceName:”adfs.domain.de” `
-ServiceAccountCredential:$serviceAccountCredential
First Time Configuration errors I ran into
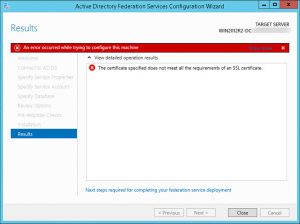
#1 Issue: After clicking Finish during the initial Configuration Wizard process I received an error stating “The Certificate specified does not meet all the requirements of an SSL Certificate.”
#1.1 Problem: Subject alternative name (SAN) value of enterpriseregistration was missing.
#1.1 Solution: Added the Subject alternative name (SAN) value of enterpriseregistration followed by the UPN suffix of my organization, i.e. enterpriseregistration.domain.com
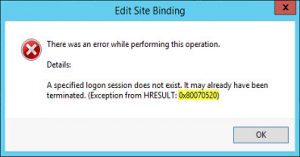
#1.2 Problem: Subject alternative name (SAN) value of enterpriseregistration was included, but certificate was imported using IIS. A subsequent https Binding on the Default Web Site was not possible due to an error A specified logon session does not exist. It may already have been terminated. (Exception from HRESULT: 0x80070520.
#1.2 Solution: Instead of importing the corresponding ADFS certificate via IIS (which can be erronous, obviously), try importing it through MMC by adding the Certificate snap-in for Local Computer; this solved it for me. Have a look at this article:
Error: “A specified logon session does not exist. It may already have been terminated. (Exception from HRESULT: 0x80070520)” binding SSL certificate using Microsoft IIS 7.0 or 7.5 server
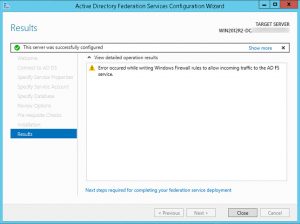
#2 Issue: Upon finishing the initial Configuration Wizard I received a warning “Error occured while writing Windows Firewall rules to allow incoming traffic to the AD FS service.”
#2 Problem: Windows Firewall service was not running as I already disabled it due to my Best Practice settings for Windows Servers as part of a domain
#2 Solution: I simply checked that AD FS is reachable for incoming traffic on port 443 from within my network as well as from external networks. Keep in mind that your Firewall/Load Balancer/NetScaler settings have to be adjusted accordingly (pls read Prepare your network infrastructure for federation servers as well).
Common issues/errors related to configuring AD FS after installation has been completed successfully
I ran into the following errors post initial configuration:
- The MSSQL$MICROSOFT##WID service was unable to log on as NT SERVICE\MSSQL$MICROSOFT##WID
- ADMIN0012: OperationFault
- ADMIN0017:
Error
The MSSQL$MICROSOFT##WID service was unable to log on as NT SERVICE\MSSQL$MICROSOFT##WID with the currently configured password due to the following error:
Logon failure: the user has not been granted the requested logon type at this computer.
Grant Log on as a Service privilege via GPO to the following users/accounts. Therefore open Default Domain Policy and Default Domain Controller Policy, navigate to Computer Configuration, Policies, Windows Settings, Security Settings, Local Policies, User Rights Assignments. Here edit Log on as a service and add the following groups:
- IIS_WPG
- NETWORK
- NETWORK SERVICE
- SERVICE
Afterwards run gpupdate /force in an elevated command prompt on the appropiate machine for these changes to take effect.
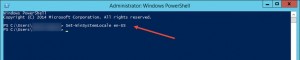
Change WinSystemLocale with Powershell:
Set-WinSystemLocale en-US
Restart server and verify WinSystemLocale with Powershell:
Get-WinSystemLocale
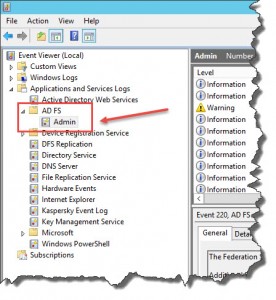
Check your Event Log under Event Viewer | Applications and Services Logs | AD FS | Admin:
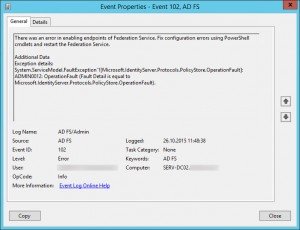
Error Event ID 102:
Log Name: AD FS/Admin
Source: AD FS
Event ID: 102
Level: Error
Keywords: AD FS
User: DOMAIN\<DomainAdminAccount>
Computer: SERV-DC02.domain.local
Description:
There was an error in enabling endpoints of Federation Service. Fix configuration errors using PowerShell cmdlets and restart the Federation Service.Additional Data
Exception details:
System.ServiceModel.FaultException`1[Microsoft.IdentityServer.Protocols.PolicyStore.OperationFault]: ADMIN0012: OperationFault (Fault Detail is equal to Microsoft.IdentityServer.Protocols.PolicyStore.OperationFault).
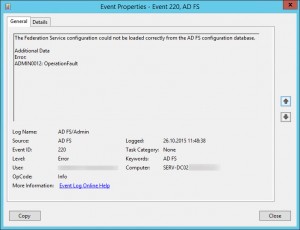
Error Event ID 220:
Log Name: AD FS/Admin
Source: AD FS
Event ID: 220
Level: Error
Keywords: AD FS
User: DOMAIN\<DomainAdminAccount>
Computer: SERV-DC02.domain.local
Description:
The Federation Service configuration could not be loaded correctly from the AD FS configuration database.Additional Data
Error:
ADMIN0012: OperationFault
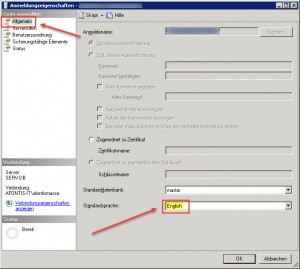
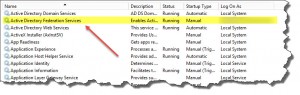
After adjusting the corresponding SQL user default language I was able to start the Active Directory Federation Service service:
If you are using SQL as the configuration store you need to check the Default Language of the user connecting to the ADFS SQL configuration DB and be sure that is set to English. ADFS and SQL are both 2012 R2.
Error Event ID 352:
Log Name: AD FS/Admin
Source: AD FS
Event ID: 352
Level: Error
Keywords: AD FS
User: DOMAIN\<DomainAdminAccount>
Computer: SERV-DC02.domain.local
Description:
A SQL operation in the AD FS configuration database with connection string Data Source=np:\\.\pipe\microsoft##wid\tsql\query;Initial Catalog=AdfsConfiguration;Integrated Security=True failed.Additional Data
Exception details:
A network-related or instance-specific error occurred while establishing a connection to SQL Server. The server was not found or was not accessible. Verify that the instance name is correct and that SQL Server is configured to allow remote connections. (provider: Named Pipes Provider, error: 40 – Could not open a connection to SQL Server)
Connect to your Windows Internal Database (WID) on Windows Server 2012
Follow these steps to connect to the Windows Internal Database on Windows 2012 machine:
- Download Microsoft SQL Server 2012 Express from the link


- Install Microsoft SQL Server Management Studio during the Install Wizard on the ADFS server (this is because of the WAP configuration being stored in the ADFS configuration database)
- Microsoft SQL Server 2012 Express requires NetFx3 feature (.Net Framework 3.5) to be enabled on the Windows 2012 sever, if you face issue enabling .Net feature follow the steps in the link
- Once installation is completed launch SQL Server Management Studio
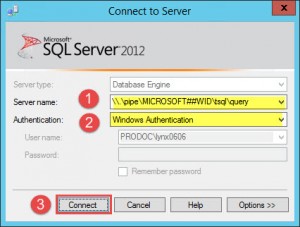
- For server name enter \\.\pipe\MICROSOFT##WID\tsql\query in case you are connecting to a Windows Server 2012 WID:

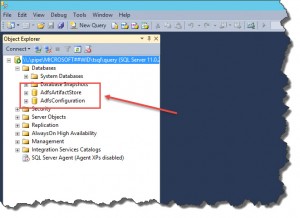
- Verify ADFS databases:

Verify your AD FS configuration:
Verify whether AD FS Configuration is working properly and whether you can launch the AD FS Management console:
- Open a browser window, in the address bar type the federation server’s DNS host name, and then append /adfs/fs/federationserverservice.asmx to it for the new federation server, for example:
https://adfs.domain.com/adfs/fs/federationserverservice.asmx
- If you see the message There is a problem with this website’s security certificate, click Continue to this website. The expected output is a display of XML with the service description document. If this page appears, IIS on the federation server is operational and serving pages successfully (Membership in Administrators, or equivalent, on the local computer is the minimum required to complete this procedure):
- Launch the AD FS Mangement console and check for any errors. In case there are not errors upon loading the MMC everything works fine:
Second option to verify whether AD FS is working as expected is to actually login and successfully authenticate against AD FS:
- Open a browser window, in the address bar type the federation server’s DNS host name, and then append /adfs/ls/IdpInitiatedSignon.aspx to it for the new federation server, for instance:https://adfs.domain.com/adfs/ls/IdpInitiatedSignon.aspx
- If you see the message There is a problem with this website’s security certificate, click Continue to this website. You will be prompted to enter your credentials:


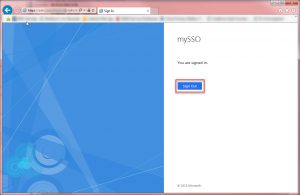
- Once you have supplied you credentials and successfully logged on you will see the following page indicating you have been successfully logged in:

For configuration of AD FS 3.0 with Citrix ShareFile and Citrix NetScaler to provide SSO access to Citrix ShareFile with Active Directory credentials, read:
Further reading:
- Microsoft Technet Checklist: Setting Up a Federation Server
- Microsoft Technet Checklist: Deploy your federation server farm on Windows Server 2012 R2
- Microsoft Checklist: Use AD FS to implement and manage single sign-on
- Deploying a federation server with a SQL database
- Microsoft Technet Blog – ADFS new features and prerequisites in Windows 2012 R2
- Microsoft Technet Blog – Configure ADFS and Device Registration service in Windows 2012 R2
- Microsoft Technet Forums – AD FS Windows 2012 R2 exception occurred in service
- ADFS 3.0 Errors 100, 102, 277
- Microsoft SQL Server Version List
- Fixing Windows Internal Database Installation Error on Windows Server 2012
- KB2832204 – “MSSQL$MICROSOFT##WID service was unable to log on as NT SERVICE\MSSQL$MICROSOFT##WID” error when you install WID in Windows Server 2012
- Technet – Troubleshooting Federation Service startup and shutdown problems
- Connect to Windows Internal Database on a Windows 2012 Machine
- Review the requirements for deploying AD FS


Pingback: Citrix NetScaler v11 – How to setup your NetScaler as an AD FS proxy – blog – Alexander Ollischer | Citrix | Microsoft