While running the Active Directory Federation Services Configuration Wizard for the first time on a newly installed Windows Server 2016, I ran into the following error after deciding to create the first federation server in a federation server farm, and creating a Group Managed Service Account (gMSA) as Service Account for my ADFS implementation:
The specified service account ‘CN=svc-ADFS-gMSA’ did not exist. Attempt to create the group Managed Service Account failed. Error: There is no such object on the server.
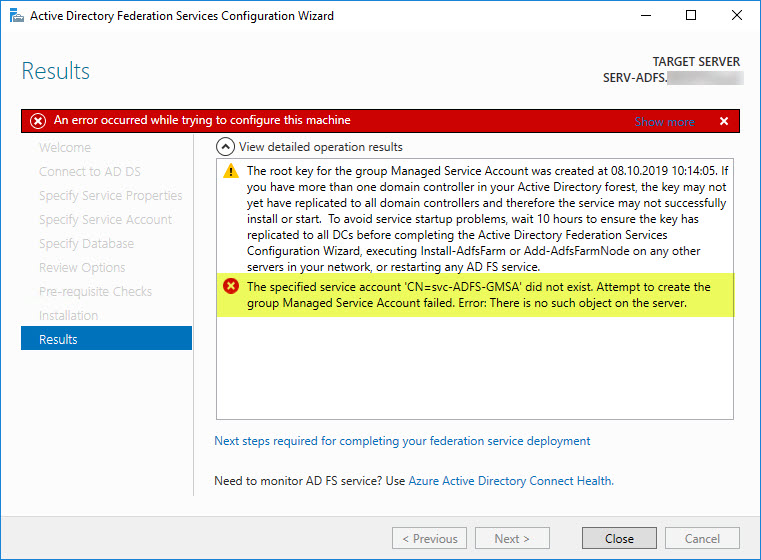
During troubleshooting it turned out that the underlying issue actually lay far deeper than expected…
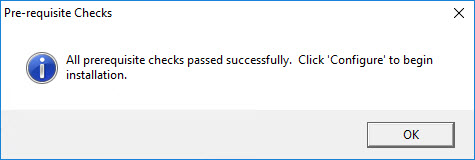
At first all prerequisites checks passed successfully:
Prior to running the Configuration Wizard I succesfully created the Key Distribution Services KDS Root Key for the gMSA by executing:
Add-KdsRootKey -EffectiveTime (Get-Date).AddHours(-10)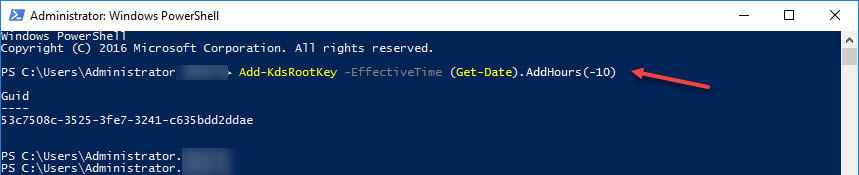
What did I miss? Well, silly me, I simply did not provision the gMSA prior to running the Configuration Wizard, though the Configuration Wizard states, that it will create a gMSA if it does not already exist:
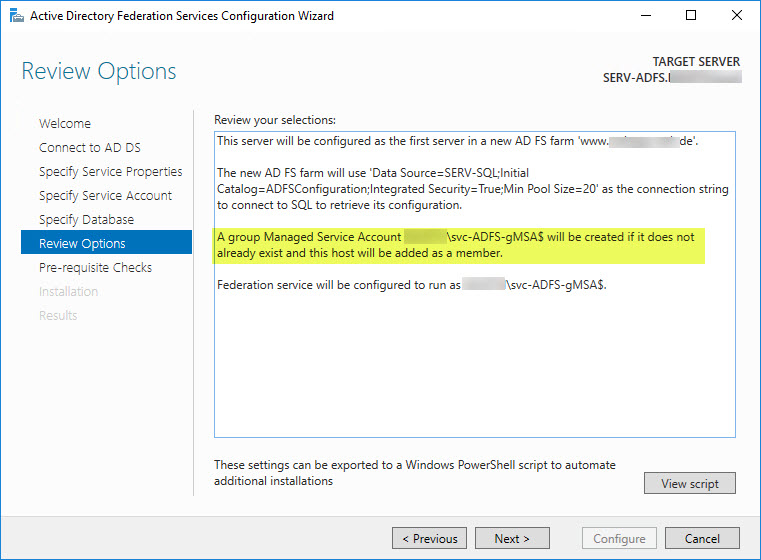
So, how do I successfully create a corresponding gMSA in order to make it work with AD FS?
You can provision a gMSA using the New-ADServiceAccount cmdlet, where domain.com ist the your own TLD:
New-ADServiceAccount -Name svc-ADFS-gMSA -DNSHostName sts.domain.com -KerberosEncryptionType RC4, AES128, AES256 -PrincipalsAllowedToRetrieveManagedPassword serv-adfs$ -ServicePrincipalNames http/sts.domain.com/domain.com, http/sts.domain.com/domain, http/sts/domaim.com, http/sts/domain -Path "CN=Users,DC=DOMAIN,DC=local"Verify whether the gMSA has been successfully provisioned in the corresponding OU provided with the -Path parameter:
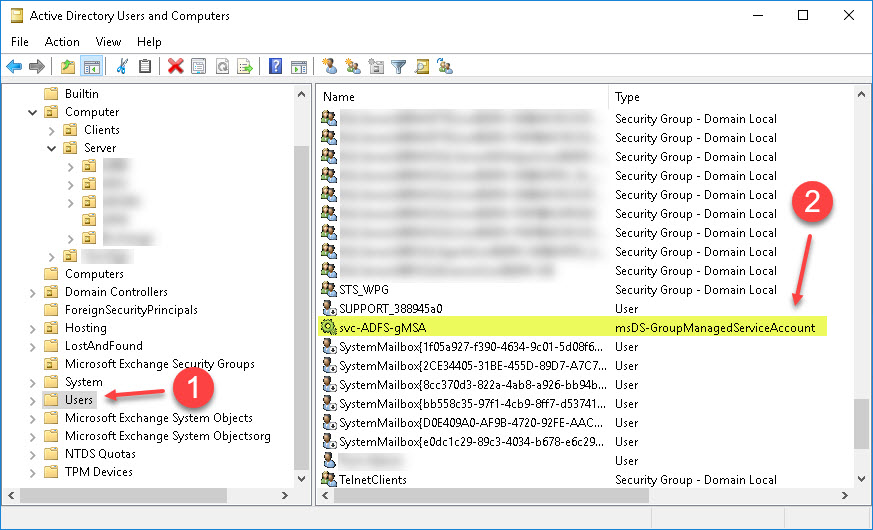
Verify whether all required Service Principal Names (SPN) have been registered and associated with the newly provisioned gMSA by executing the following command:
setspn /l svc-ADFS-gMSAAfter running the Configuration Wizard again it still fails with an error stating:
The system cannot find the file specified
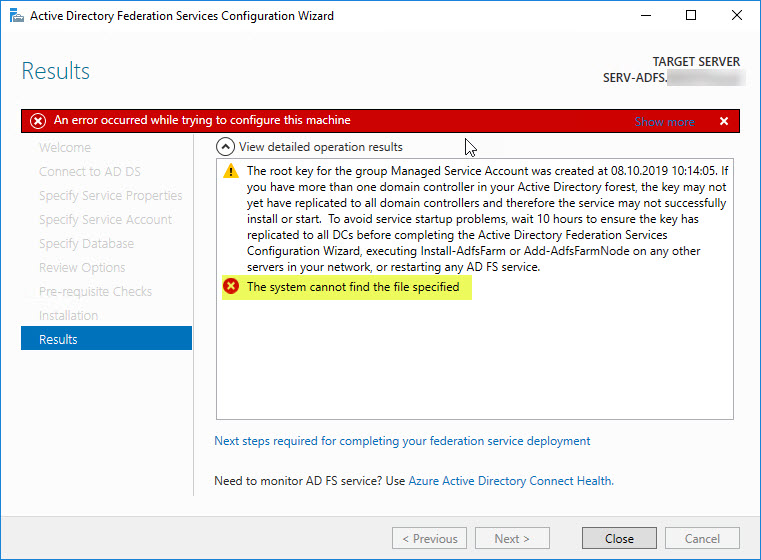
Doing a Little Research resulted in “the GMSA was moved from the Managed Service Accounts container in Active Directory” and “make sure you have a Managed service account group object in ADUC. (not an OU)”. Checking my Active Directory I realized that the required container Managed Service Accounts is actually missing! And I was unable to identify the reason why it was missing in the first place. Looking into my Deleted Objects container came up … empty.
So, how do I successfully re-create a corresponding Managed Service Accounts container in order to make it work with AD FS?
Further researching revealed I had to re-create a corresponding container with ADSIEdit named “Managed Service Accounts” and ensure ist security properties are correctly set to “Enable Inheritance”.
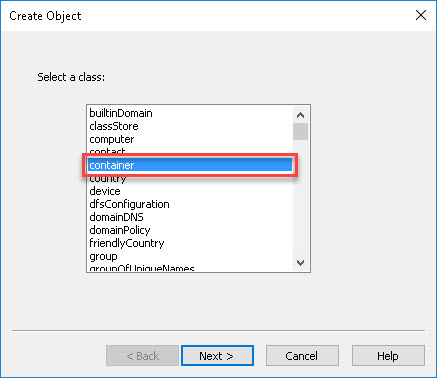
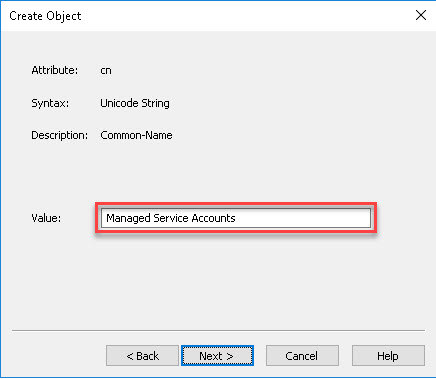
Then I deleted my previously provisioned gMSA:
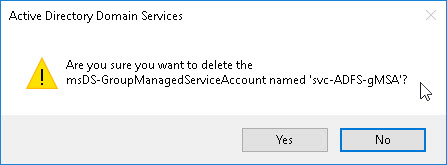
After that I ran the AD FS Configuration Wizard again and it was completed successfully:

Checking the AD FS Service as well as the corresponding Event Log showed that all went well:
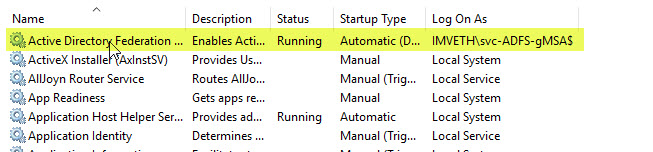
Further reading:
- Microsoft – AD FS Requirements
- Microsoft – Create the Key Distribution Services KDS Root Key
- Microsoft – Getting Started with Group Managed Service Accounts
- 250 Hello – How To Install AD FS 2016 For Office 365
- TechNet – AD FS (3.0) for Windows Server 2012 R2 Troubleshooting: Configuration with GMSA fails with ‘The system cannot find the file specified’ and other errors
- Microsoft Forums Thread – 2012 R2/ADFS with Group Managed Service Account

