After upgrading my existing and fully functional NetScaler v10.5 Build 57.7 to the latest v11.0 Build 55.23 and implementing Unified Gateway for XenMobile and XenDesktop, my users were unable to SAML authenticate with ShareFile, i.e.
- by using their MDX wrapped ShareFile app on iOS devices and locking it into an endless authentication loop without any errors:
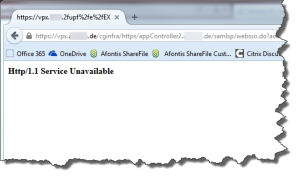
- by using their ShareFile Outlook Plugin in order to send Download and/or Upload links as they received an error stating Authentication Error – http/1.1 Service Unavailable while trying to utilize the Browser Login included with the ShareFile Outlook Plugin Configuration Wizard:
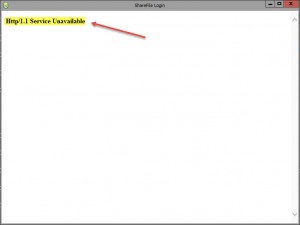
- by authenticating to our company’s custom ShareFile SAML Login page via Browser:
We’ve implemented a Custom Login Page for ShareFile as described in this article:
The Login button redirects to https://mysubdomain.sharefile.com/saml/login which in return redirects to my AppController’s ShareFile SAML authentication Web/SaaS … and the NetScaler Login page should be displayed, but instead gave me an error:
Authentication Flow:
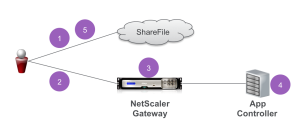
“The following diagram represents the flow of events for user authentication when XenMobile is used as a SAML identity provider:
- A user navigates to https://subdomain.sharefile.com/saml/login
- ShareFile redirects to https://NSGatewayFQDN/cginfra/https/AppController/samlsp/webssp.do?action …
- NetScaler Gateway displays a log on form to the user, who supplies ShareFile log on information.
- The authenticated user is logged on to AppController through single sign-on. AppController silently returns a SAML assertion to the user.
- The SAML assertion is passed to subdomain.sharefile.com to complete the authentication. The user is then presented with their ShareFile folders at subdomain.sharefile.com.
All ShareFile clients can leverage XenMobile for user authentication using this deployment.”
Obviously there was something wrong with my ShareFile SAML authentication configuration. Thus I had a closer look at it by using the following troubleshooting methodology to investigate all parts involved (have a look at the Further Reading section at the end of this blog for all things ShareFile and SAML):
- ShareFile Control Plane (WebUI)
- AppController v9.0.0.97000
- NetScaler v11 Build 55.23
1. ShareFile Control Plane (WebUI)
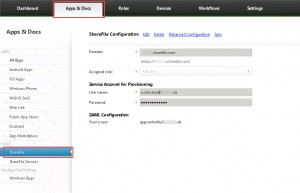
As AppController can be configured as a SAML IDP for ShareFile. Verify your ShareFile Single Sign-On Login URL by going to https://<MySubdomain>.sharefile.com, logging in with administrative privileges, navigating to Admin => Configure Single Sign-On => Login URL:
https://vpx.mydomain.de/cginfra/https/appController2.mydomain.de/samlsp/websso.do?action=authenticateUser&app=ShareFile_SAML_SP&reqtype=1&nssso=true
2. AppController v9.0.0.97000
In AppController you have to configure SAML SSO for ShareFile MDX Apps. You can use AppController along with Worx Home to SSO to ShareFile MDX wrapped applications, i.e. Worx Home obtains a SAML token for the ShareFile login using AppController as an IDP.
Verify that
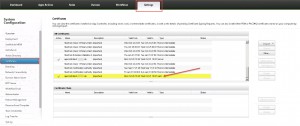
- a corresponding SAML authentication server certificate has been installed and is valid as well as trusted by NetScaler and ShareFile:
- your AppController has been successfully added to ShareFile as an SAML authentication entity:
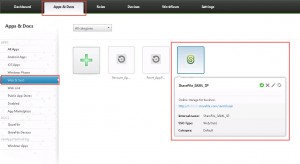
- a ShareFile SAML Login Web/SaaS application has been added and configured:
3. NetScaler v11 Build 55.23
The following configuration is required on NetScaler to support the use of AppController as a SAML Identity Provider (IDP):
- disable the default behavior for requests that come through the /cginfra path
- create a ShareFile Session Policy and Request Profile
- configure policies on the NetScaler Gateway vServer
Verify Other Settings:
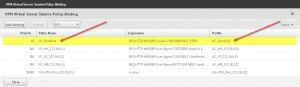
Verify ShareFile Session Policy and Profile bound to the NetScaler Gateway vServer:
Session Policy Expression:
REQ.HTTP.HEADER Cookie CONTAINS NSC_FSRD
Request Profile Settings:
| Tab | Option | Override Global | Value |
|---|---|---|---|
| Client Experience | Home Page | Y | None |
| Client Experience | Session Time Out (mins) | Y | 1 |
| Client Experience | Single Sign On to Web Applications | Y | n/a |
| Client Experience | Credential Index | Y | PRIMARY |
| Published Applications | ICA Proxy | Y | ON |
| Published Applications | Web Interface Address | Y | |
| Published Applications | Single Sign-on Domain | Y |
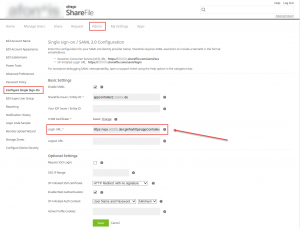
Everything seems to be configured as expected and it still didn’t work. After doing some more research I found out that the newly added UG Content Switching vServer Session Policy Expression was missing my ShareFile’s Single Sign-On Login URL as has been configured by adding AppController as a valid SAML authentication entity:
prior:
is_vpn_url || HTTP.REQ.URL.PATH.SET_TEXT_MODE(IGNORECASE).STARTSWITH(“/Citrix/Demo”)
afterwards:
is_vpn_url || HTTP.REQ.URL.PATH.SET_TEXT_MODE(IGNORECASE).STARTSWITH(“/Citrix/Demo”) || HTTP.REQ.URL.PATH.SET_TEXT_MODE(IGNORECASE).STARTSWITH(“/cginfra/https/<FQDN of my internal AC>“)
You have to add the URL part followed right after your NetScaler Gateway’s public URL, e.g.
- Public NetScaler URL: https://vpx.mydomain.com
- ShareFile SSO Login URL: https://vpx.mydomain.com/cginfra/https/appController2.mydomain.com/samlsp/websso.do?action=authenticateUser&app=ShareFile_SAML_SP&reqtype=1&nssso=true
- simply add: /cginfra/https/appController2.mydomain.com as part of the Expression mentioned above
Then I tried to access my ShareFile SAML Login page via browser once more. I successfully got redirected to my NetScaler Login, entered my credentials, and was then authenticated and redirected to ShareFile.
My ShareFile Outlook Plugin worked as well again:
Further reading:
- Configure ShareFile Single Sign-On with XenMobile 9
- Configure ShareFile Single Sign-On with XenMobile 10
- Configure ShareFile Single Sign-On with NetScaler
- Citrix Blogs – Mobility Experts Team: XenMobile Sharefile Mobile App SSO using SAML
- Configuring ShareFile and SAML Walkthrough
- Citrix Discussions – NetScaler 11 (55.23) Unified Gateway, StoreFront 3.0 & Receiver 4.3
- ShareFile Custom Login Screen