During implementing quite some XenMobile 10.x solutions in the last couple of months I came across some issues that caused quite some headaches. Therefore I’d like to document and share my lessons learned in this new blog.
As all my implementations were with existing NetScaler 10.x configurations already in place, I was not able to follow all those XenMobile 10.x installation and configuration guides out there by the book. All of those blogs and guides have one thing in common: they assume your start from scratch with both XenMobile 10.x and NetScaler 10.x and thus miss the point in merging XenMobile 10.x requirements with NetScaler 10.x, i.e. adding all those nasty MDM/MAM LB VIPs, DNS records, firewall rules, certificates, Session Policies and Profiles, et al.
I’m trying to shed some light on how to add a new XenMobile 10.x installation to an already existing NetScaler Gateway configuration.
This blog is comprised of the following topics:
Work in Progress
As implementing and configuring XenMobile can be quite a huge and complex task, I intend to update this article on a regular basis in order to get as close to a comprehensive guide as possible regarding this topic.
For starters I’d like to recommend the following blogs for all those people out there who start from scratch with both XenMobile and NetScaler, as they provide loads of information on prerequisites and all things required for a (almost) hazzle free implementation:
- Bas van Kaam – XenMobile prerequisits, what do we need and how does it all fit together?
- Citrix XenMobile – Lessons Learned in real life
- Citrix eDocs – XenMobile Server 10.3.x
- Citrix eDocs – XenMobile Server 10.3.x Architecture Overview
- Citrix eDocs – XenMobile Server 10.3.x Port Requirements
- Citrix eDocs – XenMobile Server 10.3.x Pre-Installation Checklist
- Anton van Pelt – Getting Started with XenMobile 10
- Citrix Reference Architecture for Mobile Device and App Management [PDF]
- Citrix Mobility Master Class Videos [YouTube]
- Citrix Blog – Mobility Experts Articles
- Citrix XenMobile – Before you get started
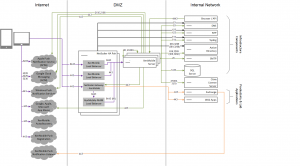
The XenMobile architecture is quite a beast to tame and needs a lot of mastering in order to beat all its intricacies. Just have a look at the following architecture diagram for a fully blown up XenMobile 10.x MDM+MAM solution placed in your internal network:
Ensure you have all this at your hands and/or access to prior to doing anything else as this will definitely delay your progress in implementing XenMobile:
- Apple Developer Account
- Apple Push Notification Certificate
- Microsoft Company Developer Account
- Google Play Store Account and Google Device ID
- Auto Discovery Actions
- DNS Registrations
- Network Connections, e.g. Firewall Rules
- Active Directory/LDAP Service Accounts
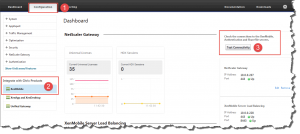
Furthemore I recommend conducting the following Connectivity Tests on both NetScaler and XenMobile Device Manager to ensure that especially required network connections can be successfully established:
- NetScaler Connectivity Tests
- can be found on NetScaler | Configuration | Integrate with Citrix Products | XenMobile | Test Connectivity:
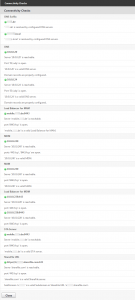
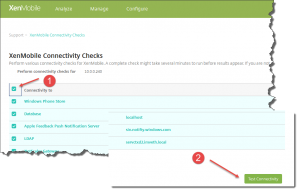
- XenMobile Connectivity Tests
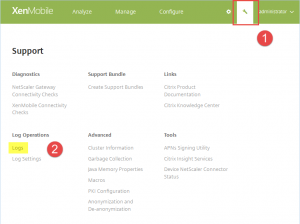
- can be found on XenMobile | Support [Wrench Tool] | Diagnostics | XenMobile Connectivity Checks:
Enable all checks listed in the XenMobile Connectivity Checks table by activating the checkbox at the top left corner, then click Test Connectivity at the bottom right corner:
Ensure that all XenMobile Connectivity Checks are greenlit, i.e. are passed successfully:
In case of an error you could left-click the corresponding table entry in order to receive further information and helpful tips on the underlying issue:
Rinse and repeat until all checks are successful.
Security:
In order to achieve the renown A+ rating by Qualys’ SSLLabs Check, you need to adjust a couple of security related settings in NetScaler. The following articles provide step-by-step instructions on how to achieve this goal:
- Citrix Blogs – Scoring an A+ at SSLlabs.com with Citrix NetScaler (the sequel)
- Citrix Blogs – Scoring an A+ at SSLlabs.com with Citrix NetScaler – 2016 update
- Anton van Pelt – Make your NetScaler SSL VIPs more secure (Updated)
After adjusting your settings you can verify the results with one of the following websites. Note that the last one (Qualys’ SSL Labs Checker) is mostly recommended:
- SSL Certificate Chain und Vulnerability Checker
- Troubleshooting Tools
The following articles and blogs are a must read for a deeper understanding of and an insight look into XenMobile 10.x
I tried to create a table showing required IP addresses as well as corresponding NetScaler Gateway vServers necessary for a working XenMobile implementation with an existing NetScaler Gateway configuration:
XenMobile and NetScaler IP Addresses
| FQDN/Hostname | Description | IP Address | Note |
|---|---|---|---|
| mobile.domain.de [internal] | XenMobile Server's FQDN, internally as well as externally; internal IP points to XenMobile Server directly | 10.0.0.240 | to make XenMobile Server reachable from internal networks (for administrative purposes); dedicated DNS address record in your internal DNS Zone |
| mobile.domain.de [external] | XenMobile Server's FQDN, internally as well as externally; external IP points to _XM_LB_MDM_XenMobile VIP directly (Ports 443 and 8443) | e.g. 1.2.3.4 (=> 10.0.0.228) | for registration and enrollment to successfully occur, traffic on both Ports 443 and 8443 must be directed to NetScaler Gateway's vServer IP address (_XM_LB_MDM_XenMobile) |
| nsip.domain.local | NetScaler Management IP | 10.0.0.252 | |
| vpx.domain.de [external] | NetScaler Gateway's external FQDN, pointing to Gateway vServer providing XenMobile Session Policy and Profile | e.g. 5.6.7.8 (=> 10.0.0.251) | existing NetScaler Gateway vServer for access to XenApp/XenDesktop as well as XenMobile resources |
| _XM_MAM_LB_10.0.0.232_8443 | XenMobile Server's LB VIP on NetScaler (Port 443), referred to NetScaler Gateway vServer (vpx.domain.de) Session Profile (Account Services Address: https://mobile.domain.de:8443) | 10.0.0.232 | |
| _XM_LB_MDM_XenMobileMDM_10.0.0.228_443 | XenMobile Server's LB VIP on NetScaler (Port 443), referred to by externally resolvable FQDN (mobile.domain.de) | 10.0.0.228 | |
| _XM_LB_MDM_XenMobileMDM_10.0.0.228_8443 | XenMobile Server's LB VIP on NetScaler (Port 8443), referred to by externally resolvable FQDN (mobile.domain.de) | 10.0.0.228 | |
| vpx.domain.de [internal] | NetScaler Gateway vServer for XenMobile access after succesful enrollment; referred to by XenMobile Server | 10.0.0.251 | provides Session Policy and Profile to redirect incoming Worx Home traffic via vpx.domain.de to XenMobile Server |
| mobile.domain.de [NetScaler DNS Address Record] | XenMobile Server's FQDN, internally as well as externally; internal IP must be resolved to _XM_MAM_LB VIP from a NetScaler point of view | 10.0.0.232 | dedicated DNS address record is required on NetScaler to directly point traffic to _XM_MAM_LB VIP |
For an already existing NetScaler Gateway configuration the following Session Policy and Profile must be added to the corresponding vServer for XenMobile traffic to be supported. Ensure checking each Session Profile/Action tab’s Advanced Settings as well:
Session Policy:
- Name: pol_Worx_home_vpx.domain.de
- Profile: ac_Worx_Home_vpx.domain.de
- Expression (in my case):
REQ.HTTP.HEADER User-Agent CONTAINS zenprise && REQ.HTTP.HEADER User-Agent CONTAINS CitrixReceiver && REQ.HTTP.HEADER X-Citrix-Gateway EXISTS || REQ.HTTP.HEADER User-Agent CONTAINS CitrixReceiver && REQ.HTTP.HEADER X-Citrix-Gateway EXISTS && REQ.HTTP.HEADER User-Agent CONTAINS Worx
You could run the following NetScaler command at CLI as well in order to create the corresponding Session Profile/Action:
#add NetScaler Gateway Session Profile
add vpn sessionAction <SessionProfileName> -splitDns BOTH -sessTimeout 1440 -splitTunnel OFF -transparentInterception ON -defaultAuthorizationAction ALLOW -SSO ON -ssoCredential PRIMARY -icaProxy OFF -ClientChoices OFF -forcedTimeout 1440 -clientlessVpnMode ON -clientlessModeUrlEncoding TRANSPARENT -SecureBrowse ENABLED -storefronturl “https://<PublicXenMobileFQDN>:8443”#add NetScaler Gateway Session Policy
add vpn sessionPolicy <SessionPolicyName> “REQ.HTTP.HEADER User-Agent CONTAINS CitrixReceiver && REQ.HTTP.HEADER X-Citrix-Gateway EXISTS” <SessionProfileName>#add NetScaler Gateway Session Policy (alternative)
add vpn sessionPolicy <SessionPolicyName> “REQ.HTTP.HEADER User-Agent CONTAINS zenprise && REQ.HTTP.HEADER User-Agent CONTAINS CitrixReceiver && REQ.HTTP.HEADER X-Citrix-Gateway EXISTS || REQ.HTTP.HEADER User-Agent CONTAINS CitrixReceiver && REQ.HTTP.HEADER X-Citrix-Gateway EXISTS && REQ.HTTP.HEADER User-Agent CONTAINS Worx” <SessionProfileName>
Session Profile / Action:
| Tab | Option | Override Global | Value |
|---|---|---|---|
| Client Experience | Split Tunnel | Y | OFF |
| Client Experience | Session Time Out (mins) | Y | 1440 |
| Client Experience | Clientless Access | Y | ON |
| Client Experience | Clientless Access URL Encoding | Y | CLEAR |
| Client Experience | Plugin Type | Y | Windows/MAC OS X |
| Client Experience | Single Sign-on to Web Applications | Y | Checkbox checked |
| Client Experience | Credential Index | Y | PRIMARY |
| Security | Default Authorization Action | Y | ALLOW |
| Security | Secure Browse | Y | ENABLED |
| Published Applications | ICA Proxy | Y | OFF |
| Published Applications | Account Services Address | Y | https://mobile.domain.de:8443 |
Keep in mind that for troubleshooting purposes it’s always recommendable to not just turn to XenMobile’s and NetScaler’s Connectivity Tests (as mentioned above), but to its logging capabilities as well, i.e. investigating its corresponding Debug Logs, Admin Audit Logs, and User Audit Logs, which can be found under in Support [Wrench Tool] | Log Operations | Logs:
Log Levels can be adjusted accordingly in Support [Wrench Tool] | Log Operations | Log Settings.
iOS Enrollment Issues:
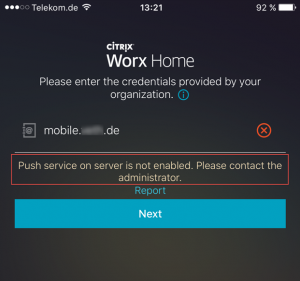
Worx Home Enrollment Error – Push service on server is not enabled. Please contact the administrator.
Make sure your XenMobile server has internet access and can reach ports TCP 2195 and TCP 2196 at destination APNs hosts using the public IP address 17.0.0.0/8. Have a look at Citrix eDocs – Port Requirements as well.
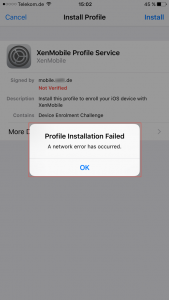
Worx Home Enrollment Error – Profile Installation Failed. A network error has occured.
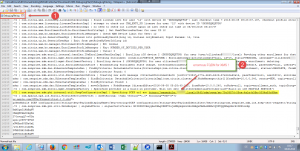
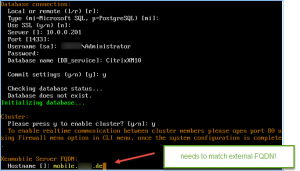
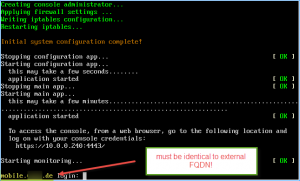
In my case it turned out that XenMobile server’s hostname deviated from my external FQDN as I configured it with an internal FQDN instead. I dug deep into XenMobile server’s Debug Log File and found the following entry while trying to enroll my iOS device:
Unfortunately you cannot change the hostname afterwards, thus requiring you to reinstall XenMobile. So make sure that during initial configuration, while defining the XenMobile Server FQDN, it equals your external FQDN:
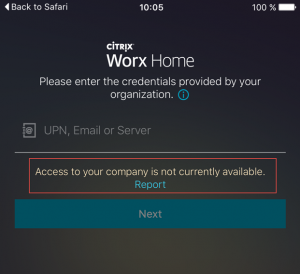
Worx Home Enrollment Error – Access to your company is not currently available.
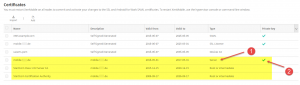
Ensure that XenMobile Server’s certificate including corresponding private key and certificate chain is complete and intact:
Best practice is to import the server certificate in PFX file format including
- private key,
- all certificates in the certification path,
- and extended properties.
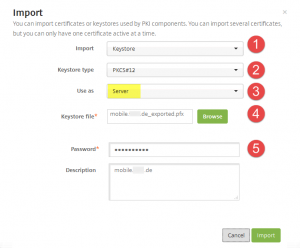
During import you should select all options as depicted:
- Import: Keystore
- Keystore type: PKCS#12
- Use as: Server
- Keystore file: <certificate.pfx>
- Password: <password to your private key>
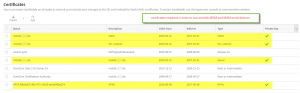
In the end it should look like this in order for you to successfully register and enroll a device with XenMobile:
- Server
- SSL Listener
- SAML
- APNs
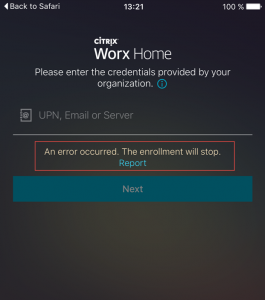
Worx Home Enrollment Error – An error occurred. The enrollment will stop.
XenMobile Debug Log: missing x-citrix-device-ID
The following bugs relate to an integration between XenMobile and NetScaler for the following versions of NetScaler when the TLS 1.2 security protocol is configured on NetScaler:
- NetScaler 11.x versions earlier than 11.0.64
- 10.5.59
- 10.5.58
Note that the issue does not arise when your XenMobile MAM deployment includes a NetScaler load balancer between the XenMobile server and NetScaler Gateway.
Communication between NetScaler Gateway and XenMobile in MAM mode fails due to issues with a backend TLS 1.2 session. As a result, users cannot download apps from the WorxStore, nor files from ShareFile, when connecting to the internal network.
or:
When updating from XenMobile 10.1 to version 10.3, if the WorxStore has a custom name, you must change the store name to the default setting of Store and deploy the setting to devices before updating. If not, the custom store name causes issues with XenMobile 10.3 enrollment, access to Worx Home and the WorxStore, and app deployment on iOS devices.
XenMobile Debug Log: URLRequestFailedMessage
Make sure your NetScaler Session Policy and Profile are configured as described above.
see: Citrix Discussions – Issue with MAM
Read Anton van Pelt’s blog on hardening your NetScaler configuration in order to receive the most precious of ratings: the Qualys SSL Labs A+ Rating. Most recommendable! And there are a lot of Citrix Mobility and NetScaler Master Class videos available on YouTube. Make sure to check them out as well!
- Integrating Xenmobile with Existing Citrix infrastructure
- Fronting XenMobile 10.x.n with NetScaler 10.5.x.n – 11.x.n
- Citrix Blogs – Mobility Experts Team: iOS WorxHome Common Issues Troubleshooting
- How to setup Citrix XenMobile 10 (including configuring NetScaler)
- Citrix XenMobile – Lessons Learned in real life
- Citrix eDocs – XenMobile Server 10.3.x
- Citrix eDocs – XenMobile Server 10.3.x Architecture Overview
- Citrix eDocs – XenMobile Server 10.3.x Port Requirements
- CTX200430 – FAQ: XenMobile 10 and NetScaler Gateway Integration
- Citrix XenMobile 10 (MDM and MAM) Behind a Single IP Address Using Citrix NetScaler
- Citrix XenMobile – Before you get started