As part of my Security Best Practices regarding Microsoft Exchange and Microsoft IIS I always implement a couple of configuration settings to harden the underlying IIS, e.g.
- disabling the “X-AspNet-Version” header,
- disabling deprecated and/or unsecure protocols,
- disabling deprecated and/or unsecure ciphers,
- setting up for SSL Perfect Forward Secrecy,
- enabling TLS 1.2,
- et al
In order to tighten your security on Exchange 2016’s IIS you should at least start with enabling HTTP Strict Transport Security (HSTS) which I’m going to describe here. As per Microsoft:
HTTP Strict Transport Security (HSTS), specified in RFC 6797, allows a website to declare itself as a secure host and to inform browsers that it should be contacted only through HTTPS connections. HSTS is an opt-in security enhancement that enforces HTTPS and significantly reduces the ability of man-in-the-middle type attacks to intercept requests and responses between servers and clients.
There are a couple of recommendations and Best Practices available that give further information on how to harden Windows Server 2012 R2/2016 as well as Exchange 2013/2016, respectively. In this article I will focus on HSTS only as I didn’t find any particular articles outlining this issue […]. Please check the Further reading section at the bottom of thids article for more information, e.g. IIS Crypto by Nartac Software:
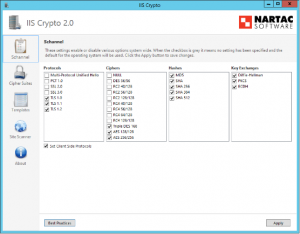
IIS Crypto is a free tool that gives administrators the ability to enable or disable protocols, ciphers, hashes and key exchange algorithms on Windows Server 2008, 2012 and 2016. It also lets you reorder SSL/TLS cipher suites offered by IIS, implement best practices with a single click, create custom templates and test your website.
You could always have a look at Center for Internet Security’s (CIS) Benchmark Documents as well, e .g. for Microsoft Exchange Server 2016, which provides a “prescriptive guidance for establishing a secure configuration posture for Microsoft Exchange Server 2016” and “was tested against Microsoft Exchange Server 2016.”
Windows Server 2012 R2 (IIS 8.5)
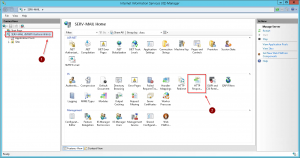
1. Open the Internet Information Services (IIS) Manager console, and click your server. Then click HTTP Response Headers in the IIS section of the middle pane:
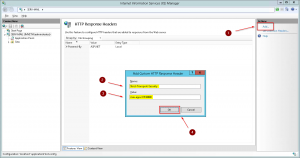
2. Click Add in the Actions pane on the right, enter the following values in the Add Custom HTTP Response Header dialogue window, then click OK:
- Name: Strict-Transport-Security
- Value: max-age=31536000
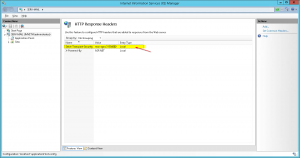
3. The newly added Custom HTTP Response Header will be added to the list of configured HTTP Response Headers in the middle pane:
4. The new setting will become effective immediately. You don’t have to iisreset your Exchange server.
Windows Server 2016 (IIS 10)
With IIS 10.0 version 1709 onwards Microsoft has implemented native HSTS support. Have a look at IIS 10.0 Version 1709 Native HSTS Support on how to configure HSTS in Windows Server 2016 version 1709+ via Powershell:
Import-Module IISAdministration
Reset-IISServerManager -Confirm:$false
Start-IISCommitDelay
$sitesCollection = Get-IISConfigSection -SectionPath "system.applicationHost/sites" | Get-IISConfigCollection
$siteElement = Get-IISConfigCollectionElement -ConfigCollection $sitesCollection -ConfigAttribute @{"name"="Contoso"}
$hstsElement = Get-IISConfigElement -ConfigElement $siteElement -ChildElementName "hsts"
Set-IISConfigAttributeValue -ConfigElement $hstsElement -AttributeName "enabled" -AttributeValue $true
Set-IISConfigAttributeValue -ConfigElement $hstsElement -AttributeName "max-age" -AttributeValue 31536000
Set-IISConfigAttributeValue -ConfigElement $hstsElement -AttributeName "redirectHttpToHttps" -AttributeValue $true
Stop-IISCommitDelay
Remove-Module IISAdministration
The new setting will become effective immediately. You don’t have to iisreset your Exchange server.
Verification
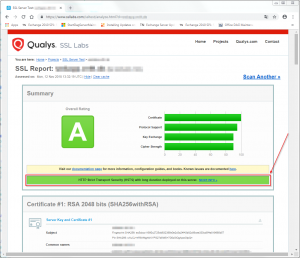
You can check whether HSTS has been successfully implemented by browsing to SSLLabs’ SSL Server Test page and enter the server’s corresponding hostname (in case it is publicly resolvable and directly reachable from the internet, which often is the case with SMBs):
That’s it! You have successfully enabled HSTS.
Further reading:
- SSL Labs Server Test – https://www.ssllabs.com/ssltest
- IIS Crypto by Nartac Software – https://www.nartac.com/Products/IISCrypto
- Microsoft Docs – IIS 10.0 Version 1709 HTTP Strict Transport Security (HSTS) Support
- Exchange Team Blog – Exchange TLS & SSL Best Practices
- Exchange Team Blog – Exchange Server TLS guidance, part 1: Getting Ready for TLS 1.2
- Exchange Team Blog – Exchange Server TLS guidance Part 2: Enabling TLS 1.2 and Identifying Clients Not Using It
- Exchange Team Blog – Exchange Server TLS guidance Part 3: Turning Off TLS 1.0/1.1
- Hardening Microsoft Exchange 2016 Server
- Frankys Web – Exchange 2016 Installation absichern (Hardening) [German]
- Alexander Hass’ Script – Setup Microsoft Windows or IIS for SSL Perfect Forward Secrecy and TLS 1.2
- Center for Internet Security (CIS) Benchmark Documents – http://benchmarks.cisecurity.org/